21 | Add to Reading ListSource URL: users.soe.ucsc.eduLanguage: English - Date: 2009-03-16 13:56:28
|
|---|
22 | Add to Reading ListSource URL: www.eset.itLanguage: English - Date: 2015-02-10 12:05:31
|
|---|
23 | Add to Reading ListSource URL: sogis.euLanguage: English - Date: 2014-08-25 01:47:51
|
|---|
24 | Add to Reading ListSource URL: ciel.orgLanguage: English - Date: 2015-06-20 18:31:18
|
|---|
25 | Add to Reading ListSource URL: www.cs.utah.eduLanguage: English - Date: 2009-04-13 14:58:42
|
|---|
26 | Add to Reading ListSource URL: kaminario.comLanguage: English - Date: 2014-01-31 16:17:48
|
|---|
27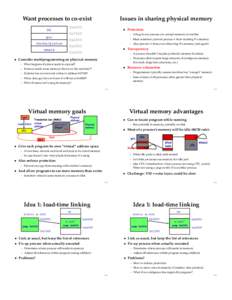 | Add to Reading ListSource URL: www.scs.stanford.eduLanguage: English - Date: 2010-01-28 18:33:49
|
|---|
28 | Add to Reading ListSource URL: www.cap-lore.comLanguage: English - Date: 2009-05-04 18:57:36
|
|---|
29 | Add to Reading ListSource URL: www.cs.berkeley.eduLanguage: English - Date: 2015-01-21 19:48:42
|
|---|
30 | Add to Reading ListSource URL: www.nanaimo.caLanguage: English - Date: 2015-04-28 13:00:27
|
|---|